

On April 27, 2021, Tenable announced that it has completed the protection of Active
Cash acquisition of Alsid, the leader of Directory. This acquisition combines the complementary advantages of two cyber security innovators and marks an important milestone in Tenable's vision, which aims to help companies understand and reduce cyber risks on the entire attack surface. At the same time, Tenable also announced the launch of Tenable.ad, which is a brand-new solution that uses Alsid technology to protect Active
Directory environment, destroys one of the most common attack paths among APT attackers and hackers.
According to Frost&According to Sullivan statistics, more than 90% of Fortune 1000 companies in the world are using Active Directory as the main method of authentication and authorization, and 80% of attacks use Active
Directory moved laterally and escalated permissions, and 60% of new malware contained code that was misconfigured against Active Directory. This risk has never been as serious as it is today. Today, more and more employees are working remotely, often using personal devices to connect to company systems. And Active
Directory also plays a key role in hosting single sign-on. Protecting accounts—employees, service contractors, temporary employees, system accounts, and others—and their cross-system access and permissions is of strategic significance to the corporate network security posture. Understanding the account’s access to the system and how these systems are related in the computing environment is a strategic and important supplement to vulnerability management and system security, and it is becoming more and more important for comprehensive risk management (especially in complex cloud and hybrid environments). necessary
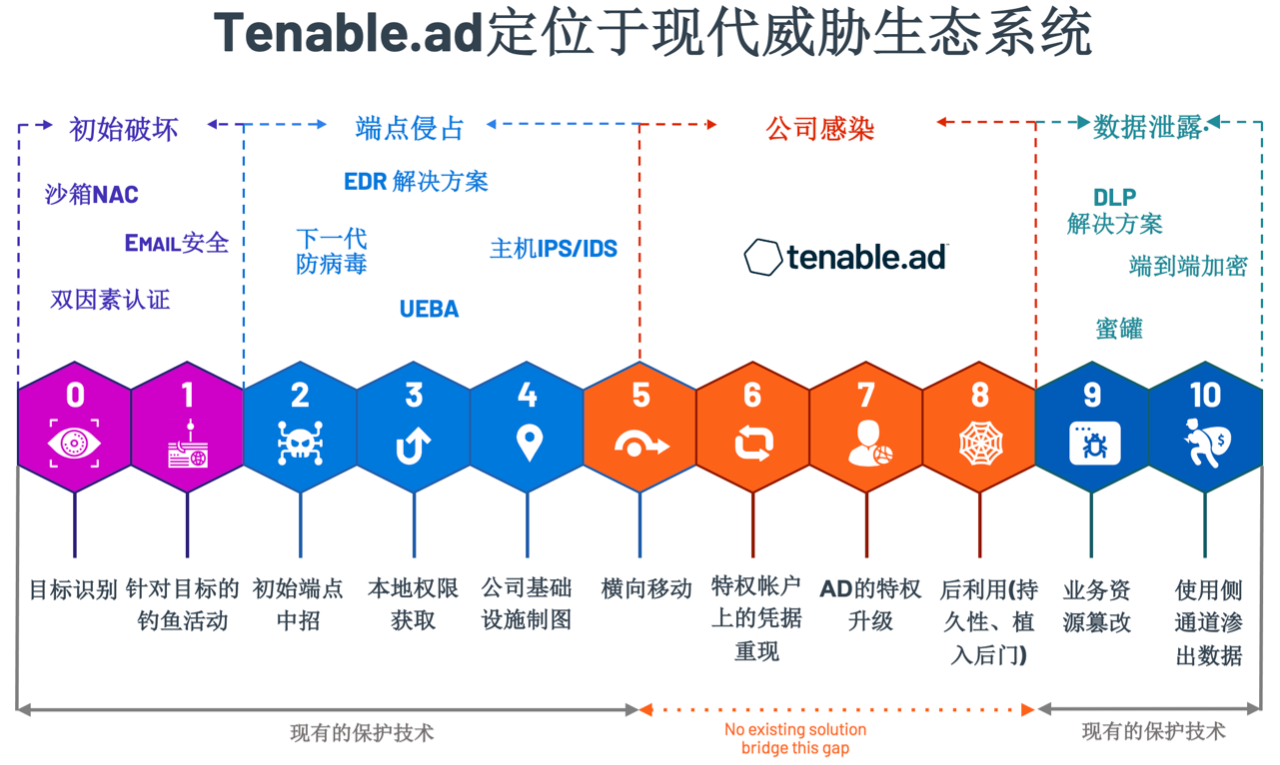
Recent incidents including the SolarWinds data breach and Microsoft Exchange hacking have highlighted the necessity of protecting Active Directory security. Successful data breaches are all from the Active Directory
The attack started with elevated privileges, followed by lateral movement, installing malware, and then stealing data.

Based on past experience, behind every headline report caused by a data breach, there is an insecure Active Directory (AD)
Deployment environment. Due to the increased complexity of domain control technology, years of misconfigurations have piled up, making it impossible for security teams to find and fix defects before they become business-affecting problems. Therefore, most enterprises are working with Active
Directory security struggles hard.
The constant changes in each company's Active Directory (AD) limit visibility to the AD attack surface and frequently introduce new attack paths. Few security teams have enough visibility and context to discover and fix AD misconfigurations and vulnerabilities.
The scale and complexity of most AD implementations make manual monitoring impractical and unable to detect attacks in real time. Incident response and threat hunting are hindered because the team cannot see all hidden misconfigurations and interrelated relationships. Although it’s vital, managing Active Directory
And to ensure its safety is extremely complicated. At the scale of a large enterprise, it is almost impossible to securely manage Active Directory without a large amount of expertise and continuous attention.
Successful violations are often accompanied by attacks on Active Directory to elevate permissions, move laterally, install malware, and filter data. Attackers can successfully hide these developments from logs and other monitoring tools because they pass Active The move of the Directory seems to be in line with existing security policies. When an attacker successfully delivers a payload that leads to data loss, extortion requirements, environmental reconstruction, or brand impact, the high cost of weaker AD security will be hit.
Through the acquisition of Alsid, Tenable has achieved an important milestone in helping companies understand and reduce cybersecurity risks on the entire modern attack surface. With Tenable.ad, you can support the delivery of risk-based Active Directory security practices.
Tenable.ad allows security and IT professionals to find and fix weaknesses in Active Directory before attackers can exploit them. It also allows incident response personnel to detect and respond to attacks when they occur.
The core work of Tenable.ad is to conduct an extremely thorough review and evaluation of every configuration setting, every entry and relationship in Active Directory. Then, it will simplify these findings and provide IT
And the security team created priority recommendations to resolve issues based on their importance, the relative ease of changing the configuration, and the relative ease of implementing the recommendations.
In addition, Tenable.ad also provides continuous monitoring of risky activities, which may let you know whether sabotage activities are in progress. The activities it monitors include:
Create a new administrator account;
Hide account
Permission changes;
Add a new group;
Add users to the group;
Create a trust relationship;
and many more.
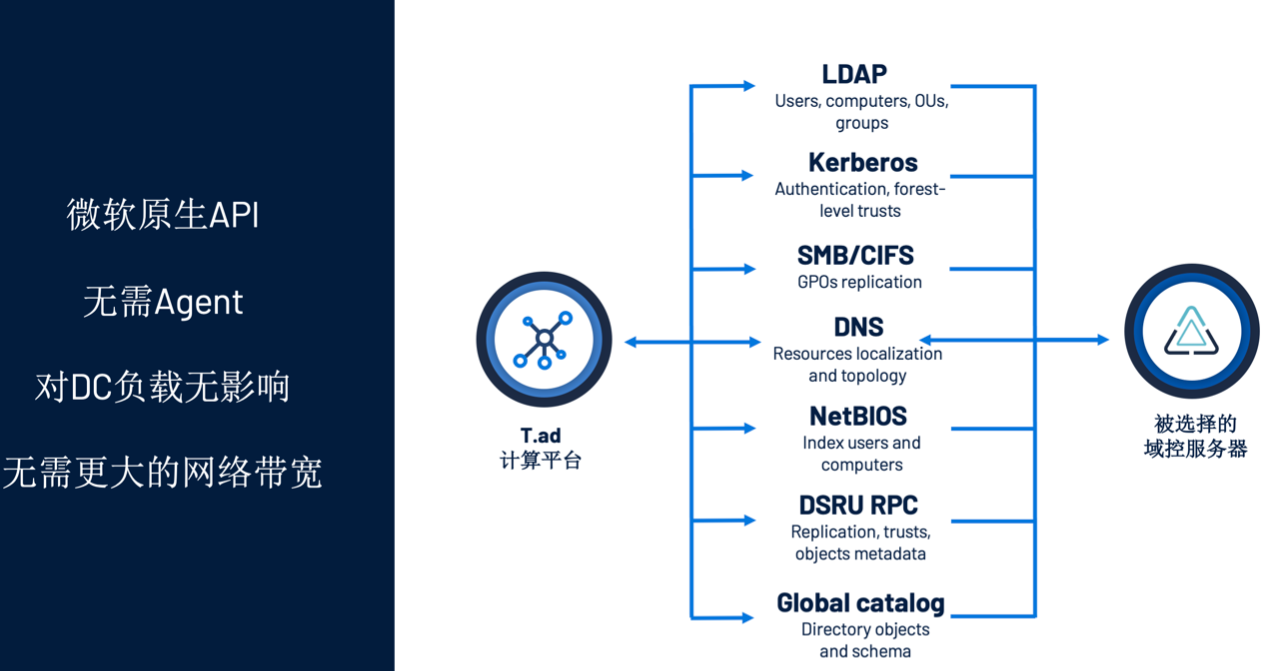
The biggest advantage of Tenable.ad is that it only requires user-level account access rights. Therefore, it is very important for IT
The organization's influence is relatively limited. Tenable.ad also does not need to install any agent on the domain controller. With the Tenable.ad platform, security professionals do not need to install any software on sensitive systems, and therefore will not cause unnecessary business operations interruption.
In addition, Tenable.ad does not need to rely on the Windows system log to work normally. This log only provides a point-in-time view of events that are happening in the system. Advanced threat technologies can already bypass it to perform attacks. In contrast, Tenable.ad relies on Active
The replication and native API functions in the Directory provide security professionals with the insights needed to protect user permissions in a rapidly changing environment.
Continuously monitor and detect Active Directory attacks, such as Golden Ticket, DCShadow, brute force, password spraying and guessing, DCSync, etc. Tenable.ad enriches your SIEM, SOC or SOAR attack insights, so you can respond quickly and stop attacks. Automatic AD attack detection reduces the monitoring burden of the security team and spends their time on other priorities.
Analyze in-depth attack details, associate object and attribute level AD configuration changes and historical behavior records, and quickly find the trace of the attacker.
